academia
A collection of works from my academic activities, including student projects I (co-)supervised.
peer-reviewed
- Turning Merge Conflicts Into Conflict-Induced VariabilityManuel Ohrndorf, Alexander Boll, Roman Bögli, and Timo KehrerIn 48th IEEE/ACM International Conference on Software Engineering: New Ideas and Emerging Results, ICSE NIER, Rio de Janeiro, Brazil, Apr 2026(forthcoming)
Merging is central to software version control, yet current techniques force developers to resolve conflicts immediately upon each merge attempt, causing constant interruptions and hampering continuous integration. Despite extensive research on advanced merging techniques, the current practice remains largely unchanged. With this paper, we propose a paradigm shift: merge conflicts shall be no longer treated as obstacles to be eliminated immediately, but as a form of software variability that explicitly captures diverging developer intentions. Such conflict-induced variability defines alternative behaviors that can be explored, analyzed, and resolved upon request, enabling deferred bulk conflict resolution based on the analysis results. With this, we open an avenue of research around a paradigm that shall preserve the practicality of today’s merging techniques, while accelerating traditional versioning workflows through increased flexibility and more effective conflict resolution.
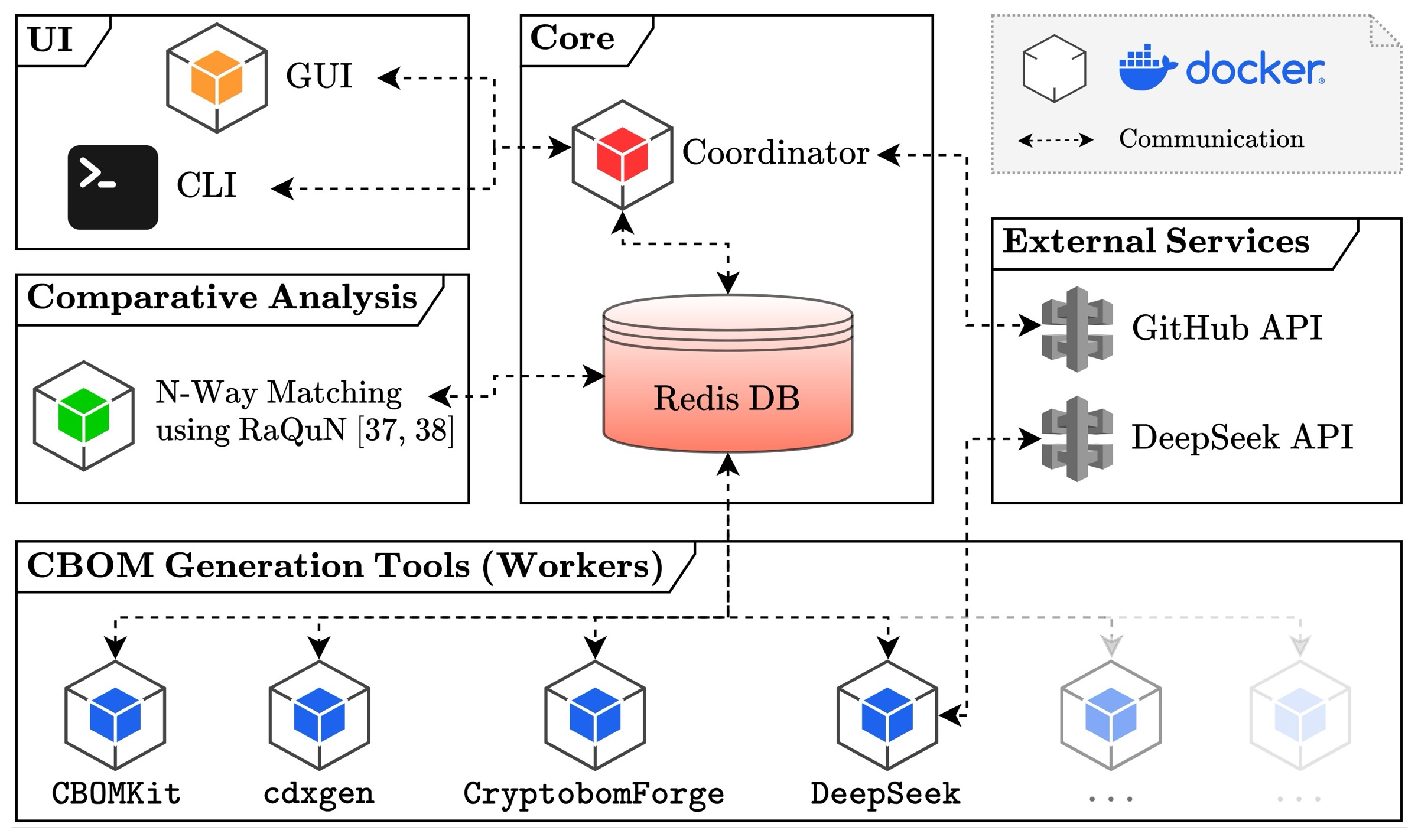
- BF-CBOM: Uncovering Cryptographic Assets Through Comparative CBOM Analysis at ScaleRoman Bögli, Jonas Spieler, and Timo KehrerIn 34th IEEE/ACM International Conference on Program Comprehension, ICPC 2026, Rio de Janeiro, Brazil, Apr 2026(forthcoming)
The advancing threat of quantum-capable adversaries accelerates the need to locate and replace vulnerable cryptographic assets in software systems. To support this transition, Cryptography Bills of Materials (CBOMs) are becoming essential for capturing and inventorying the cryptographic footprint of software systems as increasingly demanded by regulators in critical domains. While first CBOM generation tools have emerged, they still lack reliable means to comprehend and analyze the cryptographic landscape of codebases. We present BF-CBOM, a first-of-its-kind framework for orchestrating various CBOM generators and analyzing their outputs, enabling holistic comprehension of the cryptographic posture of software projects. BF-CBOM offers a containerized environment designed to accommodate the heterogeneous toolchains of such generators, executes them on GitHub code repositories, and aggregates their outputs for comparative investigation in a unified analysis layer. Our preliminary study reveals striking discrepancies between generated CBOMs, underscoring the need for systematic evaluation. BF-CBOM supports researchers with cryptographic reports, practitioners through CI/CD integration, and tool developers by providing performance feedback relative to other generators.
- Towards Systematic Treatment of Community-Driven VariabilityRoman BögliIn ICSE-Companion ’26: 2026 IEEE/ACM 48th International Conference on Software Engineering, Rio de Janeiro, Brazil, Jan 2026(forthcoming)
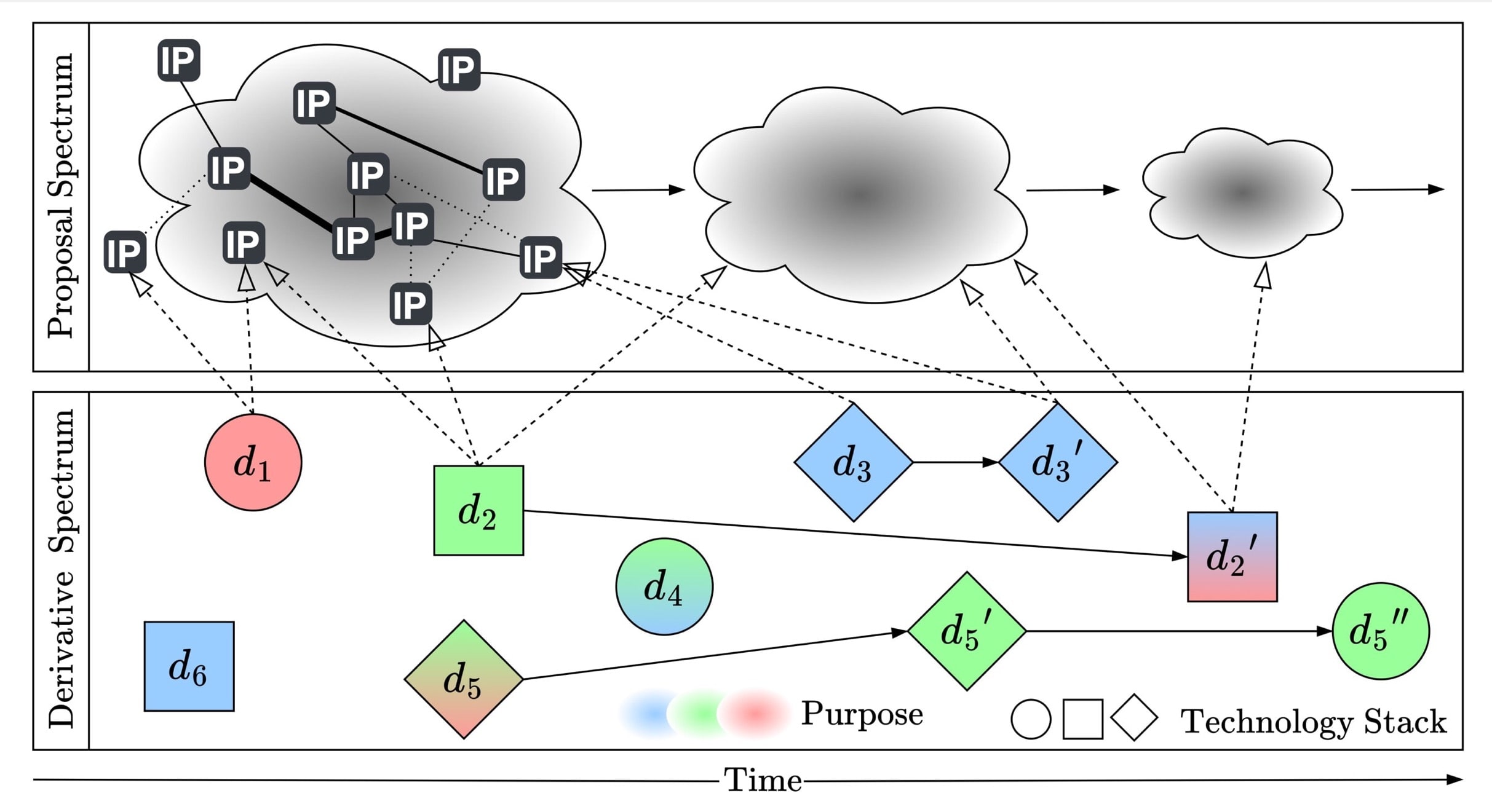
Modern decentralized software ecosystems such as Bitcoin evolve through crowdsourced improvement proposals (IPs) that are continuously shaped and autonomously implemented by independent actors. As a result, these ecosystems exhibit Community-Driven Variability (CDV), a novel paradigm that extends beyond traditional variability-intensive systems and introduces new challenges that remain unsolved. With this thesis, we approach these challenges and step forward to enable a holistic, systematic treatment of this problem space. This includes (i) establishing a modeling formalism that adequately captures the versatility of CDV ecosystems, (ii) providing tool support for automated model extraction from the large corpus of open-source IP data, and (iii) integrating these mined models with analyses of concrete implementation derivatives.
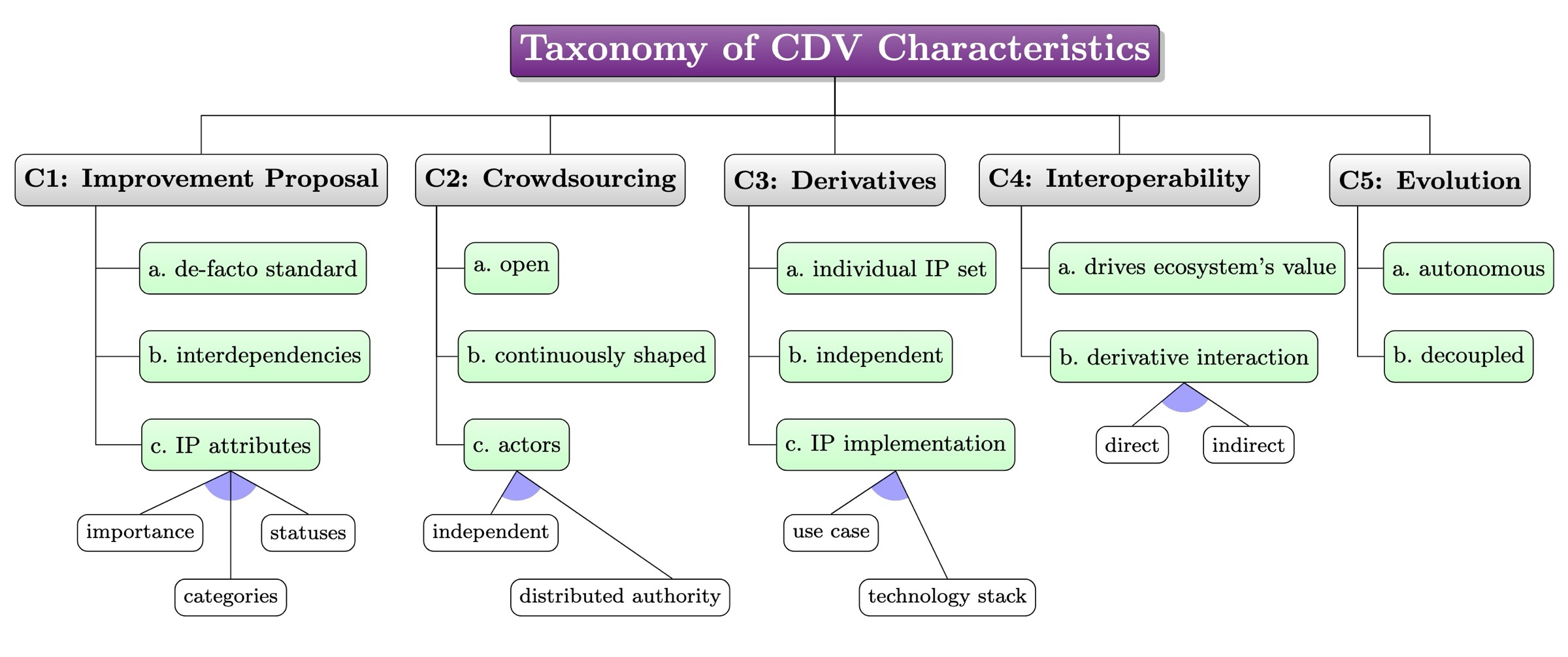
- Community-Driven Variability: Characterizing a new Software Variability ParadigmRoman Bögli, Alexander Boll, Alexander Schultheiß, and Timo KehrerAutomated Software Engineering, Jan 2026(forthcoming)
Both software engineering researchers and practitioners have increasingly shifted their focus from single software systems to software families, reflecting the need for software industrialization through systematic reuse of implementation artifacts. Interestingly, several vibrant ecosystems produce software families in a radically different way than classical variability-intensive systems, notably software product lines (SPLs). The Bitcoin community, for instance, evolves its ecosystem through crowdsourced improvement proposals being continuously shaped and autonomously implemented by independent actors. While this novel paradigm of Community-Driven Variability (CDV) has proven effective for driving flourishing technologies like Bitcoin and others, it also comes with unique challenges calling for novel solutions. In this paper, we define the key characteristics of ecosystems exposing CDV and derive a taxonomy that hierarchically decomposes each characteristic into constituting sub-characteristics. Building on the taxonomy, we conduct a systematic analysis of 14 software ecosystems to evaluate the presence and nature of CDV. We highlight the novel problems they face, such as the lack of ecosystem overview, difficulties in impact assessment, misalignment between proposals and implementations, and interoperability breakdowns – challenges that transcend classical variability management. Based on the problem analysis, we outline our research vision to tackle these challenges, including a sketch of concrete starting points for technical solutions. While classical SPLs and CDV ecosystems differ drastically, we believe that feature-oriented modeling and analysis offers promising concepts for addressing CDV challenges without enforcing product-line processes. Conversely, the unique demands of CDV can inspire advances in variability research with impact beyond its original domains.
- Beyond Software Families: Community-Driven VariabilityRoman Bögli, Alexander Boll, Alexander Schultheiß, and Timo KehrerIn Companion Proceedings of the 33nd ACM International Conference on the Foundations of Software Engineering (FSE), Trondheim, Norway, Jun 2025
Both software engineering researchers and practitioners have increasingly shifted their focus from single software systems to software families, reflecting the need for software industrialization through systematic reuse of implementation artifacts. Interestingly, several vibrant ecosystems produce software families in a radically different way than classical variability-intensive systems, notably software product lines. The Bitcoin community, for instance, evolves its ecosystem through openly shared improvement proposals being continuously shaped and autonomously implemented by independent actors. While this novel paradigm of community-driven variability (CDV) has proven effective for driving flourishing technologies like Bitcoin and others, it also comes with unique challenges calling for novel solutions. In this paper, we define the key characteristics of ecosystems exposing CDV, highlight the novel problems they face, and outline our respective research vision.
@inproceedings{10.1145/3696630.3728501, author = {B{\"{o}}gli, Roman and Boll, Alexander and Schultheiß, Alexander and Kehrer, Timo}, title = {Beyond Software Families: Community-Driven Variability}, year = {2025}, month = jun, publisher = {{ACM}}, booktitle = {Companion Proceedings of the 33nd ACM International Conference on the Foundations of Software Engineering (FSE)}, location = {Trondheim, Norway}, series = {FSE 2025}, url = {https://doi.org/10.1145/3696630.3728501}, doi = {10.1145/3696630.3728501}, } - Temporal Logics Meet Real-World Software Requirements: A Reality CheckRoman Bögli, Atefeh Rohani, Thomas Studer, Christos Tsigkanos, and 1 more authorIn 2025 IEEE/ACM 13th International Conference on Formal Methods in Software Engineering (FormaliSE), Apr 2025
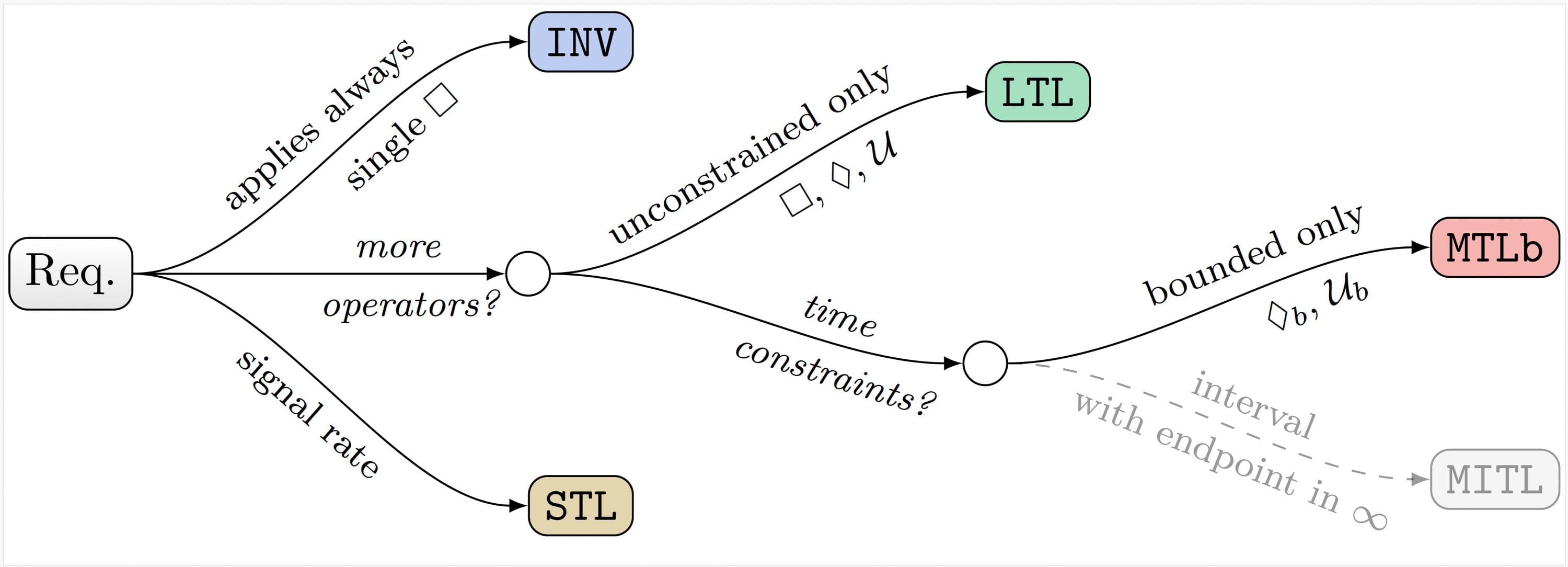
Reasoning on the behavior of software systems is challenging, especially in critical domains such as aerospace. Transitioning from natural language to formal specifications enables long-pursued activities such as modeling, synthesis, and verification. Temporal logics are often used in this regard, each with different operators, expressiveness or associated implementations. However, a significant gap exists between the theoretical capabilities of the logics applied in formal methods and the practical needs for specifying real-world requirements. This paper addresses this gap through a case study of SpaceWire, a standard specification for a data-handling communication protocol often adopted on spacecraft and other on-board systems. We extract 89 software requirements exhibiting temporal behavior and transcribe them into logic-based formalizations using different established temporal logics, maximizing natural encoding. We analyze the suitability of the chosen logics for formalizing the selected software requirements to reason about potential implications for both researchers and practitioners.
@inproceedings{10.1109/FormaliSE66629.2025.00014, author = {B{\"{o}}gli, Roman and Rohani, Atefeh and Studer, Thomas and Tsigkanos, Christos and Kehrer, Timo}, title = {Temporal Logics Meet Real-World Software Requirements: A Reality Check}, booktitle = {2025 IEEE/ACM 13th International Conference on Formal Methods in Software Engineering (FormaliSE)}, pages = {74-85}, year = {2025}, month = apr, url = {https://doi.org/10.1109/FormaliSE66629.2025.00014}, doi = {10.1109/FormaliSE66629.2025.00014}, } - A Systematic Literature Review on a Decade of Industrial TLA+ PracticeRoman Bögli, Leandro Lerena, Christos Tsigkanos, and Timo KehrerIn Integrated Formal Methods - 19th International Conference, IFM 2024, Manchester, UK, November 13-15, 2024, Proceedings, Nov 2024
TLA+ is a formal specification language used for designing, modeling, documenting, and verifying systems through model checking. Despite significant interest from the research community, knowledge about usage of the TLA+ ecosystem in practice remains scarce. Industry reports suggest that software engineers could benefit from insights, innovations, and solutions to the practical challenges of TLA+. This paper explores this development by conducting a systematic literature review of TLA+’s industrial usage over the past decade. We analyze the trend in industrial application, characterize its use, examine whether its promised benefits resonate with practitioners, and identify challenges that may hinder further adoption.
@inproceedings{DBLP:conf/ifm/BogliLTK24, author = {B{\"{o}}gli, Roman and Lerena, Leandro and Tsigkanos, Christos and Kehrer, Timo}, editor = {Kosmatov, Nikolai and Kov{\'{a}}cs, Laura}, title = {A Systematic Literature Review on a Decade of Industrial TLA+ Practice}, booktitle = {Integrated Formal Methods - 19th International Conference, {IFM} 2024, Manchester, UK, November 13-15, 2024, Proceedings}, series = {Lecture Notes in Computer Science}, volume = {15234}, pages = {24--34}, publisher = {Springer}, year = {2024}, month = nov, url = {https://doi.org/10.1007/978-3-031-76554-4\_2}, doi = {10.1007/978-3-031-76554-4\_2}, timestamp = {Wed, 08 Jan 2025 21:12:55 +0100}, biburl = {https://dblp.org/rec/conf/ifm/BogliLTK24.bib}, bibsource = {dblp computer science bibliography, https://dblp.org}, }
other
- Masters Thesis
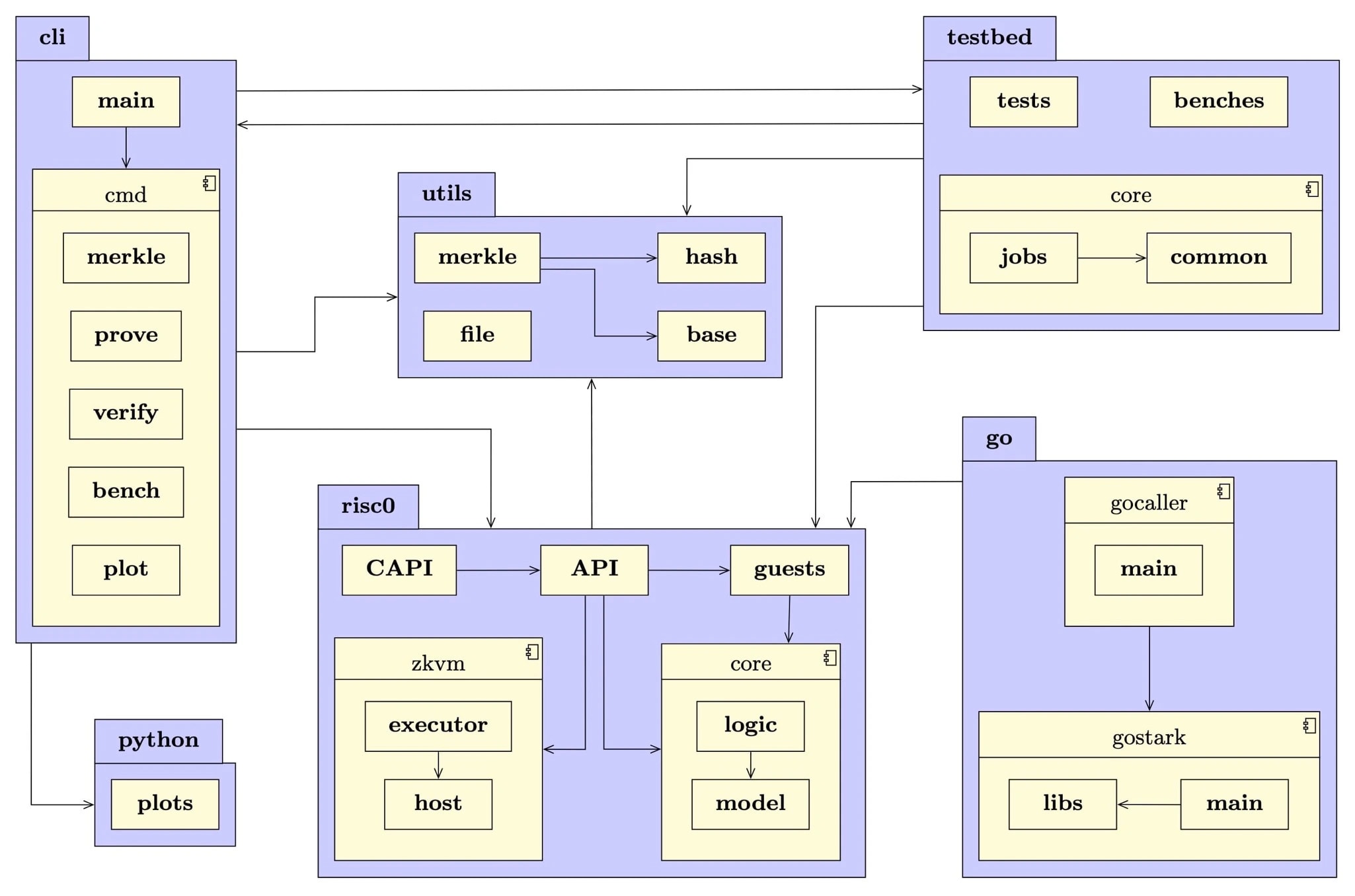 Assessing RISC Zero Using ZKit: An Extensible Testing and Benchmarking Suite for ZKP FrameworksRoman BögliJan 2024
Assessing RISC Zero Using ZKit: An Extensible Testing and Benchmarking Suite for ZKP FrameworksRoman BögliJan 2024This thesis summarizes the most important properties of ZKPs and highlights the key differences between two famous implementation families, namely SNARK and STARK systems. Also, we provide a summary of promising software libraries or frameworks that help to create and verify ZKPs. Next, we analyze risc0 in detail using the above-addressed use case of an IP, i.e., proving a the inclusion of leaf in a Merkle tree data structure. Therefore, we propose the concept of ZKit, an extensible toolkit for testing and benchmarking various ZKP frameworks. Besides a Command Line Interface (CLI) to execute parameterized benchmarks or generate Merkle tree test data, it also contains functionality to define and exchange IPs in a unified way. Furthermore, ZKit exemplifies how ZKP circuits written in Rust can be ported to the Go ecosystem through a wrapper library. This portability facilitates the integration of ZKPs in existing Go projects such as for example the Fabric Token-SDK (FTS). Last but not least, we share our risc0 benchmark results on IPs in two different settings. In the first setting, we measured the performance and allocated resources to create one proof for a single IP. In the second setting, we aggregate or batch multiple IPs in a single proof. We compare and interpret the results of these two settings at the end and state our recommendations that we drew from it.
@mastersthesis{bogli2024AssessingRISCZero, type = {Masters Thesis}, title = {Assessing {{RISC Zero}} Using {{ZKit}}: {{An Extensible Testing}} and {{Benchmarking Suite}} for {{ZKP Frameworks}}}, author = {Bögli, Roman}, editora = {El Khiyaoui, Kaoutar and De Caro, Angelo and Caracas, Alexandru}, editoratype = {collaborator}, date = {2024-01-23}, month = jan, year = {2024}, language = {English}, school = {Eastern Switzerland University of Applied Science}, url = {https://eprints.ost.ch/id/eprint/1158/}, } - Semester Project
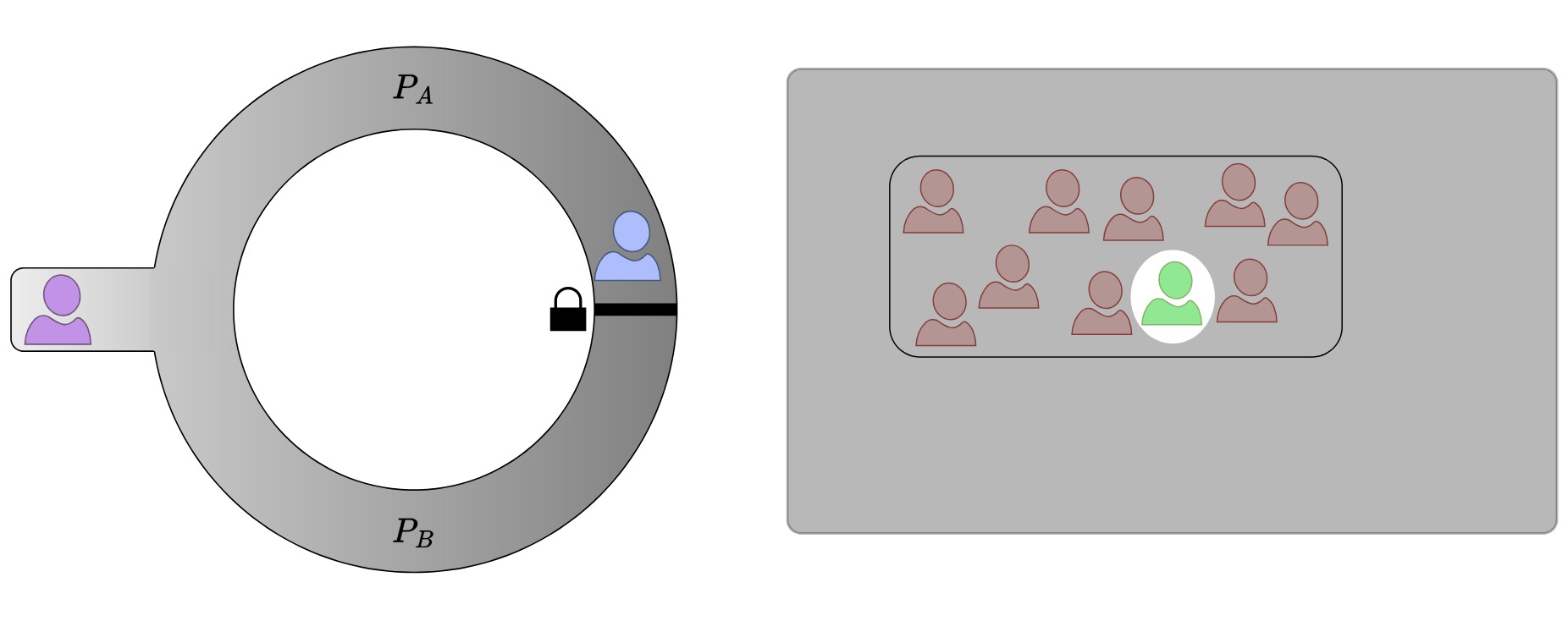 Zero-Knowledge Inclusion ProofsRoman BögliAug 2023
Zero-Knowledge Inclusion ProofsRoman BögliAug 2023This work discusses a solution for implementing a zero-knowledge inclusion proof using existing software components, referred to as automation frameworks. In the beginning, the use case that necessitates such proofs is stated together with establishing the contextual backdrop. This includes elaborating essential prerequisites such as cryptographic hash functions, commitment schemes, and Merkle trees. Furthermore, it presents an overview of zero-knowledge proof systems, detailing their core characteristics, analogies, and real-world applications. The discussion delves into the two prominent implementation families, namely zkSNARK and zkSTARK, emphasizing their distinguishing features. To ensure resistance against potential threats originating from quantum computers, the proposed approach centers on utilizing non-interactively employed zkSTARK proofs enabled through the Fiat-Shamir transformation. Finally, this work formally states the objective of the zero-knowledge inclusion proof for the specific use case and proposes an algorithmic specification. A curated selection of promising automation frameworks with the potential to facilitate the objective’s implementation is presented, with in-depth scrutiny applied to two specific frameworks: RISC Zero and the Winterfell. The work concludes by discussing initial experiences with these frameworks and outlining future endeavors to chart the path towards implementing a minimal viable product.
@misc{bogli2023ZeroKnowledgeInclusionProofs, title = {Zero-{Knowledge} {Inclusion} {Proofs}}, language = {EN}, publisher = {Eastern Switzerland University of Applied Science}, author = {Bögli, Roman}, collaborator = {El Khiyaoui, Kaoutar and De Caro, Angelo and Purandare, Mitra}, date = {2023-08-21}, month = aug, year = {2023}, url = {https://eprints.ost.ch/id/eprint/1121/}, } - Semester Project
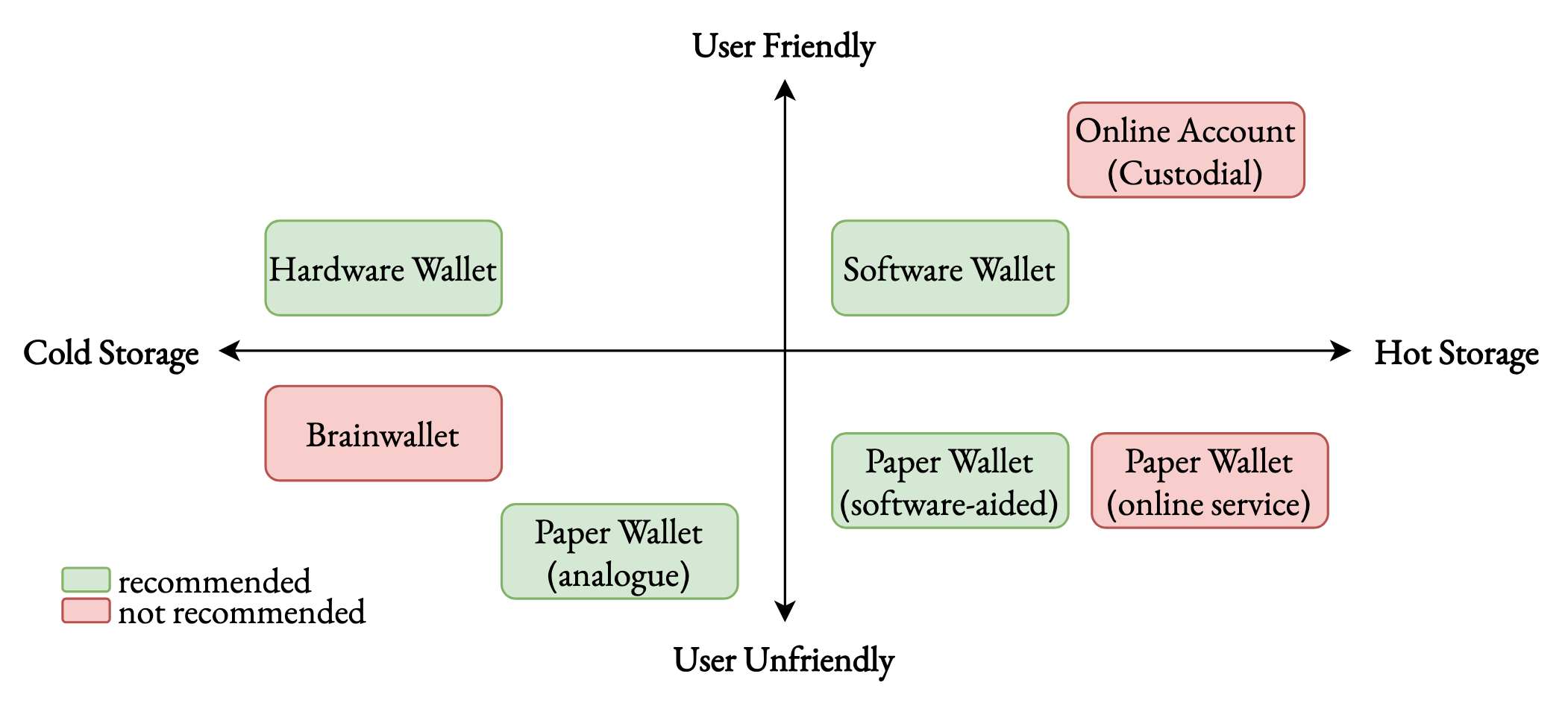 A Security Focused Outline on Bitcoin WalletsRoman BögliMar 2023
A Security Focused Outline on Bitcoin WalletsRoman BögliMar 2023The famous electronic peer-to-peer cash system called Bitcoin is an open-source protocol allowing individuals to store and transact units of the same named currency. Private and public key cryptography plays a central role in this value transfer system, which implies the importance of professionally managing the information about such keys. This work elaborates on the essential prerequisites to understand this relatively new technology that combines elements from the fields of computer science, cryptography, mathematics, and game theory. In doing so, crucial general and Bitcoin-specific terms are defined and contextually explained. The central part of this work addresses the outline of different Bitcoin interaction means, commonly known as wallets. The structure of the presented wallet types orients itself alongside a potential user’s experience. Besides defining explanations and examples of use cases, this work outlines advantages and disadvantages concerning security and privacy. The start concerns two wallets that target beginners in the field of Bitcoin. The concept of online accounts is elaborated and attention is drawn to the inherent need to trust when using them. Also, the relatively primitive type of paper wallets is surveyed. For a more intermediate interaction with this peer-to-peer cash system, the concept of software wallets, in general, is explained and examples are provided. The bridge from single-address paper wallets will be drawn to the more sophisticated multi-address wallets enabled through rooted key derivation techniques. Designated computer devices that solely serve the purpose of managing keying material, known as hardware wallets, represent another intermediate wallet type discussed in this work. Last, advanced topics are discussed that further leverage the security and privacy of someone’s interaction with Bitcoin. One concerns the setup of a self-managed Bitcoin full node. This undertaking not only harmonies with the concept of verification over trust but also allows for the complete exclusion of any third party between wallet communication. Equally advanced is the concept of multi-signature wallets, which is discussed at the end of this work.
@misc{bogli2023SecurityFocusedOutline, title = {A {Security} {Focused} {Outline} on {Bitcoin} {Wallets}}, language = {en}, publisher = {Eastern Switzerland University of Applied Science}, author = {Bögli, Roman}, collaborator = {Weiler, Nathalie}, date = {2023-03-07}, month = mar, year = {2023}, url = {https://eprints.ost.ch/id/eprint/1103/}, } - Bachelors Thesis
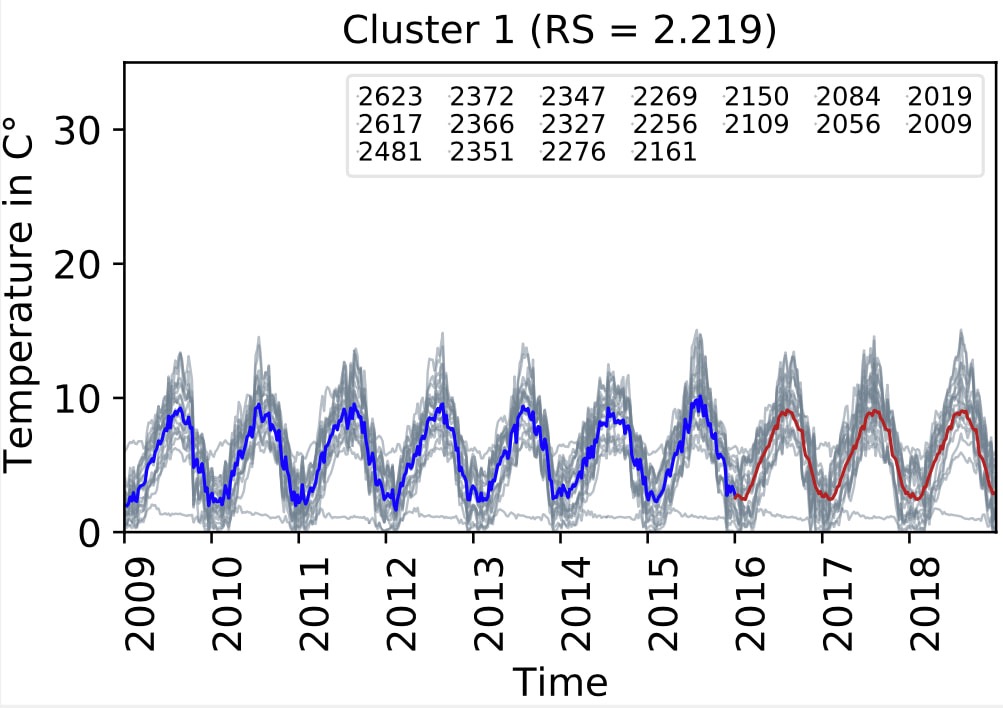 Time Series Clustering with Water Temperature DataRoman BögliAug 2020
Time Series Clustering with Water Temperature DataRoman BögliAug 2020This thesis studies three different approaches to cluster long-term water temperature data using the unsupervised pattern recognition method called hierarchical clustering. The cluster qualities are assessed using internal cluster validity indexes and forecast deviation analysis.
@thesis{bogli2020TimeSeriesClustering, type = {Bachelors Thesis}, title = {Time {Series} {Clustering} with {Water} {Temperature} {Data}}, language = {English}, school = {University of Applied Sciences and Arts Northwestern Switzerland (FHNW)}, author = {Bögli, Roman}, collaborator = {Bigler, Vidushi C.}, date = {2020-08-07}, month = aug, year = {2020}, url = {https://studierendenprojekte.wirtschaft.fhnw.ch/view/61}, } - Semester Project
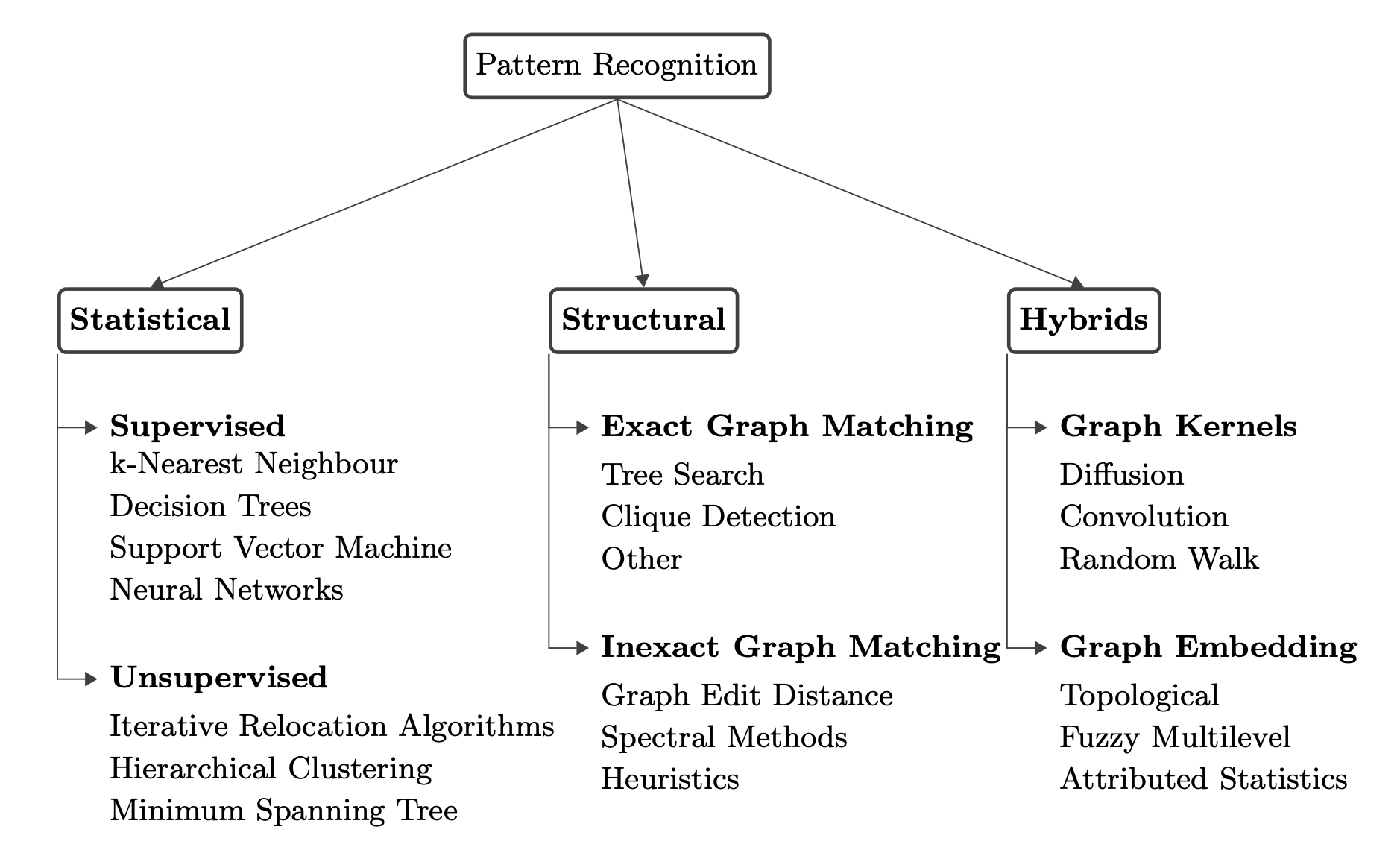 Statistical vs. Structural Pattern Recognition - A SurveyRoman BögliDec 2019
Statistical vs. Structural Pattern Recognition - A SurveyRoman BögliDec 2019This paper surveys the different approaches in pattern recognition (PR). After the fundamental idea of PR is stated, a taxonomy landscape is presented which divides into three families, namely statistical, structural, and hybrids. The first represents a well-researched topic in PR which engendered popular and efficient supervised and unsupervised pattern discovery algorithms. The second family addresses techniques to find patterns in structurally represented data using graphs that allow capturing the information of relationships among objects. Thirdly, the hybridization of the prior two families will be discussed. This includes the elaboration of transformation methods that allow to embed a graph into a vector space using graph kernels or graph embedding.
@misc{bogli2019StatisticalVsStructural, type = {Literature {Review}}, title = {Statistical vs. {Structural} {Pattern} {Recognition} - {A} {Survey}}, language = {English}, publisher = {University of Applied Science and Arts Northwestern Switzerland (FHNW)}, author = {Bögli, Roman}, date = {2019-12-24}, month = dec, year = {2019}, }
supervised
- Masters ThesisDynamic CBOM: A Survey of Cryptographic Bill of Materials Generation and a Runtime Proof-of-ConceptWilliam Anze DanFeb 2026
Rapid progress in quantum computing and the threat of “harvest-now, decrypt-later” make migration to post-quantum cryptography (PQC) a near-term priority. Effective migration, however, depends on knowing exactly where and how cryptography is used across software landscapes. A Cryptography Bill of Materials (CBOM) provides that visibility, but current practice is fragmented: the scopes of existing tools are limited to certain languages and libraries and generating high-fidelity CBOMs is hard due to the scattering nature of cryptography assets. This thesis makes two contributions. First, it presents – to our knowledge – the first explorative survey and taxonomy of CBOM generation techniques by reviewing existing tools including IBM’s CBOMkit, CycloneDX’s cdxgen and looking into similar area "code analysis". We cover traditional static analysis including regex-based signatures and Abstract Syntax Tree (AST)/Code Property Graph (CPG) pattern matching, Machine Learning (ML) static analysis, instrumentation, and program slicing (static and dynamic). Second, we develop a proof-of-concept dynamic CBOM generator that reports cryptographic assets at runtime via instrumentation, avoiding heavyweight static analysis while capturing algorithms, parameters, and call sites during execution. Together, the survey and working prototype contribute to advancing the CBOM field and thereby further pave the way towards effective PQC migration.
@thesis{Dan2026_DynamicCBOM, type = {Masters Thesis}, title = {Dynamic CBOM: A Survey of Cryptographic Bill of Materials Generation and a Runtime Proof-of-Concept}, language = {English}, school = {University of Bern}, author = {Dan, William Anze}, supervisor = {Kehrer, Timo and Bögli, Roman}, date = {2026-02-01}, month = feb, year = {2026}, } - Masters ThesisGaining Context About Bitcoin Improvement Proposals: Mining and Visualizing Bitcoin Improvement ProposalsMohammad EglilFeb 2026
Bitcoin is an ever-evolving peer-to-peer payment system governed by a decentralized community. To develop a clear and concise process defining how Bitcoin functions, the Bitcoin Improvement Proposals (BIPs) were introduced. In a documented and decentralized manner, BIPs describe how Bitcoin should function, similar to software specification documents. However, a rapidly growing number of proposals has made it increasingly difficult to maintain a concise representation of authorship and dependency relationships. This thesis examines the structure and development of BIPs to provide a clearer understanding of how Bitcoin evolves over time. To this end, a data processing pipeline was implemented to collect and parse BIP documents to derive context and insights regarding Bitcoin evolution and the surrounding community. This pipeline combines explicit extraction methods with large language models to identify both explicit and implicit references between various proposals. The processed data are then analyzed using different visualization techniques to obtain a deeper understanding of BIPs and their interdependencies. The results reveal clear patterns in authorship concentration, layer flows, and dependency structures. A small number of authors tend to contribute the majority of BIPs, certain layers progress differently throughout the BIP lifecycle, and specific proposals form key nodes within the dependency network. Significant disparities are identified between what is stated in the preamble of a BIP document and what is actually referenced within the document itself. These insights provide a transparent overview of the BIP landscape and highlight the central structures shaping Bitcoin’s technical development alongside its decentralized community. Additionally, the pipeline’s design supports the continuous evaluation of historical changes, making potential future evolutions more visible.
@thesis{Eglil2026_BIPs, type = {Masters Thesis}, title = {Gaining Context About Bitcoin Improvement Proposals: Mining and Visualizing Bitcoin Improvement Proposals}, language = {English}, school = {University of Bern}, author = {Eglil, Mohammad}, supervisor = {Kehrer, Timo and Bögli, Roman}, date = {2026-02-09}, month = feb, year = {2026}, } - Bachelors ThesisQualitative Analyse der Verwendung von Dentalsoftware in der SchweizFabian SchwarzJan 2026
Praxismanagementsoftware für Zahnärzte umfasst Funktionen zur Verwaltung von Patientendaten, zur Kommunikation, zum Rechnungswesen sowie zur Praxisorganisation. Aufgrund ihrer tiefen Integration in die Arbeitsabläufe sind Zahnarztpraxen heute in hohem Masse von diesen Systemen abhängig. Diese Arbeit untersucht den Einsatz von Praxismanagementsoftware in Schweizer Zahnarztpraxen. Dabei sollen konkrete und tatsächlich bestehende Anforderungen von Zahnärzten an Praxismanagementsoftware identifiziert werden. Die Erkenntnisse basieren auf qualitativen Befragungen in Form von Interviews mit Zahnärzten und Domänenexperten. Darüber hinaus können die Ergebnisse Zahnärzte dazu anregen, den eigenen Umgang mit Dentalsoftware kritisch zu reflektieren. Auf Basis einer vorgängigen Literatur- und Softwarerecherche werden im ersten Teil der Arbeit Forschungsfragen entwickelt, welche die Grundlage für die anschliessend durchgeführten leitfadengestützten Interviews bilden. Im Hauptteil der Arbeit werden die Ergebnisse aus Interviews mit fünf Zahnärzten sowie zwei Domänenexperten dargestellt. Die Auswertung zeigt, dass zwischen den eingesetzten Softwaresystemen teilweise Unterschiede bestehen. Gleichzeitig lassen sich auch Gemeinsamkeiten identifizieren, insbesondere wiederkehrende Defizite in Bezug auf Benutzerfreundlichkeit und Übersichtlichkeit. Ein zentrales Ergebnis ist der ausgeprägte Wunsch der befragten Zahnärzte nach einer stärkeren Unterstützung bei administrativen und bürokratischen Tätigkeiten. Abschliessend werden die Perspektiven der Zahnärzte und der Domänenexperten gegenübergestellt und in einen gemeinsamen Kontext eingeordnet. Dabei zeigen sich sowohl übereinstimmende als auch divergierende Meinungen und Wünsche hinsichtlich Praxismanagementsoftware in der Zahnmedizin.
@thesis{Schwarz2026_Dentalsoftware, type = {Bachelors Thesis}, title = {Qualitative Analyse der Verwendung von Dentalsoftware in der Schweiz}, language = {German}, school = {University of Bern}, author = {Schwarz, Fabian}, supervisor = {Kehrer, Timo and Bögli, Roman}, date = {2026-01-30}, month = jan, year = {2026}, } - Bachelors ThesisAGAT: Ein heuristischer Algorithmus zur präferenzbasierten Gruppenbildung mit fester GruppengrössePatrick RüegseggerAug 2025
Die automatisierte, präferenzbasierte Gruppenbildung mit fester Gruppengrösse ist ein NP-schweres Partitionierungsproblem. Diese Arbeit entwickelt und evaluiert mit dem AGAT-Algorithmus einen neuen, heuristischen Lösungsansatz. Der Algorithmus kombiniert agglomeratives hierarchisches Clustering mit neu entwickelten, deterministischen Reparaturstrategien, um die strikte Grössenanforderung zu erfüllen. Ein flexibles Präferenzmodell ermöglicht dabei die Verarbeitung gemischter Attributtypen sowie die Optimierung auf Ähnlichkeit (homogene Kriterien) und Unterschiedlichkeit (heterogene Kriterien). Eine systematische Evaluation von zehn unterschiedlich konfigurierten Varianten des Algorithmus identifizierte eine klare Leistungshierarchie. Die Konfiguration aus der mittelwertbasierten UPGMA-Verknüpfungsmethode und der konstruktiven Merge-Reparatur lieferte durchweg die qualitativ besten Ergebnisse. Die Einordnung der Ergebnisse zeigt die Überlegenheit des Ansatzes: Die erzeugten Lösungen übertreffen systematisch zufallsbasierte Partitionen und nähern sich für kleine Problemgrössen dem globalen Optimum an. Die Arbeit validiert den zweistufigen Ansatz somit als effektive und robuste Methode und liefert eine datengestützte Empfehlung für den optimalen Praxiseinsatz.
@thesis{Ruegsegger2025_AGAT, type = {Bachelors Thesis}, title = {AGAT: Ein heuristischer Algorithmus zur präferenzbasierten Gruppenbildung mit fester Gruppengrösse}, language = {German}, school = {University of Bern}, author = {Rüegsegger, Patrick}, supervisor = {Kehrer, Timo and Bögli, Roman}, date = {2025-08-20}, month = aug, year = {2025}, } - Bachelors ThesisCBOMbench: A Cryptographic Bill of Materials Evaluation and Benchmarking ToolSimon EgliJul 2025
Quantum computing poses a threat to the current cryptographic infrastructure, necessitating a migration to post-quantum algorithms. This transition demands cryptographic agility, which involves the systematic identification and audit of cryptographic assets or components across entire software system landscapes. Cryptographic Bills of Materials (CBOMs) facilitate this process by automating the discovery and management of such cryptographic assets. However, the effectiveness of the available CBOM generation tools has yet to be validated. This thesis introduces an extensible benchmarking framework for systematically evaluating these generation tools, providing a comparative analysis of three different CBOM generation approaches. We implemented CBOMbench, a modular evaluation framework for CBOM tool assessment. Using this framework, we evaluated three approaches to CBOM generation: IBM’s CBOMkit, CycloneDX’s cdxgen and DeepSeek’s API. Our benchmark analyzed these tools on 100 Java repositories, measuring tool performance across functional capabilities, component detection and runtime characteristics. The results show significant variations in tool capabilities. DeepSeek achieved an 87% non-empty CBOM coverage in an average of 24.7 seconds. Cdxgen detected 38’354 components in total, but exhibited parsing failures and high variability in execution time. CBOMkit identified 2’327 components with specific categorization and predictable scaling behavior. Further analysis reveals that despite universal CycloneDX compliance claims, substantial variations in metadata field usage and component categorization required tool-specific parsing logic. This suggests that the current standards provide insufficient prescriptive guidance. This research establishes a foundation for evidence-based CBOM tool development by providing the first systematic evaluation framework and empirical analysis of current capabilities. As organizations increasingly recognize the importance of becoming cryptographically agile for post-quantum readiness, this work enables informed tool selection and supports the maturation of cryptographic asset management practices, which are essential for long-term cybersecurity.
@thesis{Egli2025_CBOMbench, type = {Bachelors Thesis}, title = {CBOMbench: A Cryptographic Bill of Materials Evaluation and Benchmarking Tool}, language = {English}, school = {University of Bern}, author = {Egli, Simon}, supervisor = {Kehrer, Timo and Bögli, Roman}, date = {2025-07-24}, month = jul, year = {2025}, } - Bachelors ThesisAn Algorithmic Approach for Solving the Grouping ProblemAndrin Müller, and Viola MeierFeb 2025
The grouping problem, a challenging combinatorial optimization problem classified as NP-hard, seeks to divide a set of objects into optimal groups while satisfying predefined constraints. This thesis explores algorithmic approaches to solve this problem for fixed group sizes and in scenarios involving must-link and cannot-link constraints, which enforce mandatory co-membership or exclusion between specific individuals. The primary focus is on developing novel methods for encoding features and constraints that minimize total intra-group distances, ensuring the desired homogeneity or heterogeneity at the feature level. One of the key contributions of this work is the development of a unified feature encoding technique that accommodates various feature types, enhancing the accuracy of member compatibility analysis by seamlessly integrating both homogeneous and heterogeneous features. Another significant contribution is the transformation of compatibility measurements into a single-objective optimization framework, which simplifies the computational process. This transformation enables the evaluation of member compatibility with greater efficiency, ensuring that the minimization of intra-group distances remains the central objective. Additionally, the thesis presents three algorithmic approaches for group assembly: Ant Colony Optimization (ACO), a customized PCKMeans clustering algorithm, and the Occurrence Ranking (OCCR) approach. Each of these algorithms provides a different strategy for solving the grouping problem and can be adapted for various optimization objectives. The effectiveness and efficiency of these algorithms are thoroughly evaluated, with performance metrics tailored specifically for group formation tasks. This evaluation demonstrates their capability to generate optimal groupings in a reasonable computational time frame. The experimental results highlight the potential applications of these methods in collaborative learning, team-building, and other domains that require structured group formation. The findings also lay the groundwork for future work, including improvements to algorithm scalability, the integration of more complex constraints, and the exploration of alternative optimization techniques.
@thesis{MuellerMeier2025_AGAT, type = {Bachelors Thesis}, title = {An Algorithmic Approach for Solving the Grouping Problem}, language = {English}, school = {University of Bern}, author = {Müller, Andrin and Meier, Viola}, supervisor = {Kehrer, Timo and Bögli, Roman}, date = {2025-02-06}, month = feb, year = {2025}, }